Managed Protection, Detection and Response (MPMDR)
Mantix4 and our Partners provide Managed Protection, Detection and Response (MPMDR) services for those clients who want a 24x7x365 helpdesk and Security Operations Center (SOC) support.
Mantix4 and our partners’ SOC operations, with operations centers throughout the United States, Canada, and Europe, will work in conjunction with your internal IT staff or can be the primary monitoring service (MSSP) for your business. Our partners additionally provide full Managed Services (MSP) should you prefer to outsource the predominance of your IT work. We can provide the entire solution set or just the pieces you need to fill your gaps.
Mantix4 Platform deploys rapidly and delivers integrated full-context visibility of Network, Behavioral, EDR/XDR, Q-Net, and other platforms generating proactive actionable Cyber Intelligence for SOC operators. Mantix4 additionally provides continuous enhanced Cyber Hygiene Assessment for endpoint and cloud services enabling incremental hardening of your IT environment against Cyber threats. Mantix4 fills a key role in the Cybersecurity solution set reducing your Risk.
Mantix4 integrates with Partners to provide next generation of National Intelligence-Grade cybersecurity protection through monitored HardSec Encryption for those who need to protect Critical Infrastructure, or meet the strictest Regulatory Compliance standards. Our simple plug and play, maintenance-free Quantum resistant solution provides AES 256 GCM Military Grade Encryption while reducing your Network Attack Surface through cloaking. And for those who, based on Risk, need lower levels of Protection, our team will work with you to get the right customized solution in place.
Communication and coaching. The Mantix4 team knows the ins and outs of the Cybersecurity environment. We will translate tech-speak to provide real-world valuable insights that will protect your data and neutralize cyber threats.
Mantix4 Platform
Mantix4’s proprietary Network iSensor (with and without Hardware options) and machine learning enhanced Network Detection and Response Software bridges the large visibility gap left by traditional security technologies. The SOC team, enabled with full-context Network and Behavioral visibility and proactive actionable Cyber Intelligence can limit and/or stop network compromises.
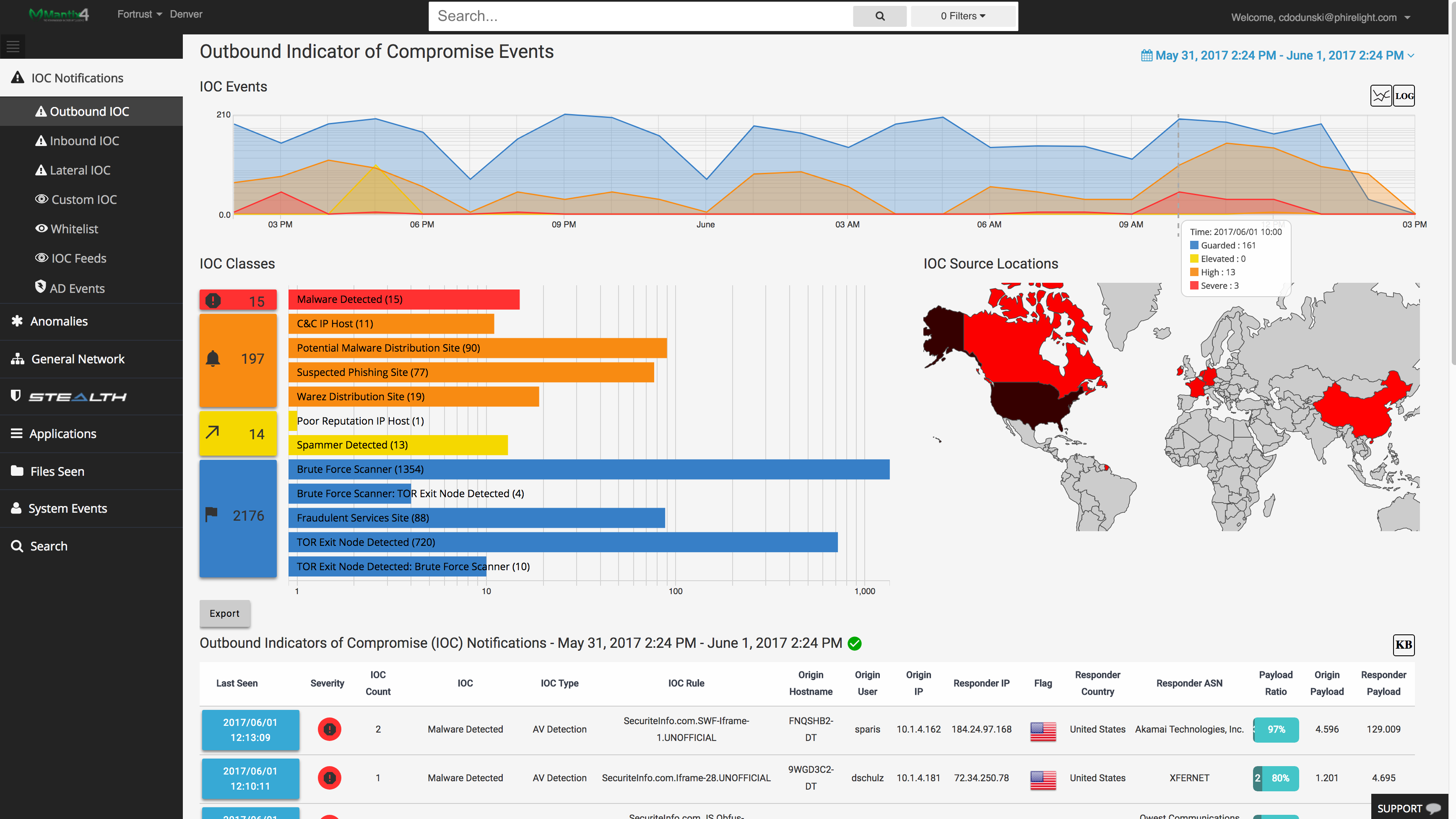
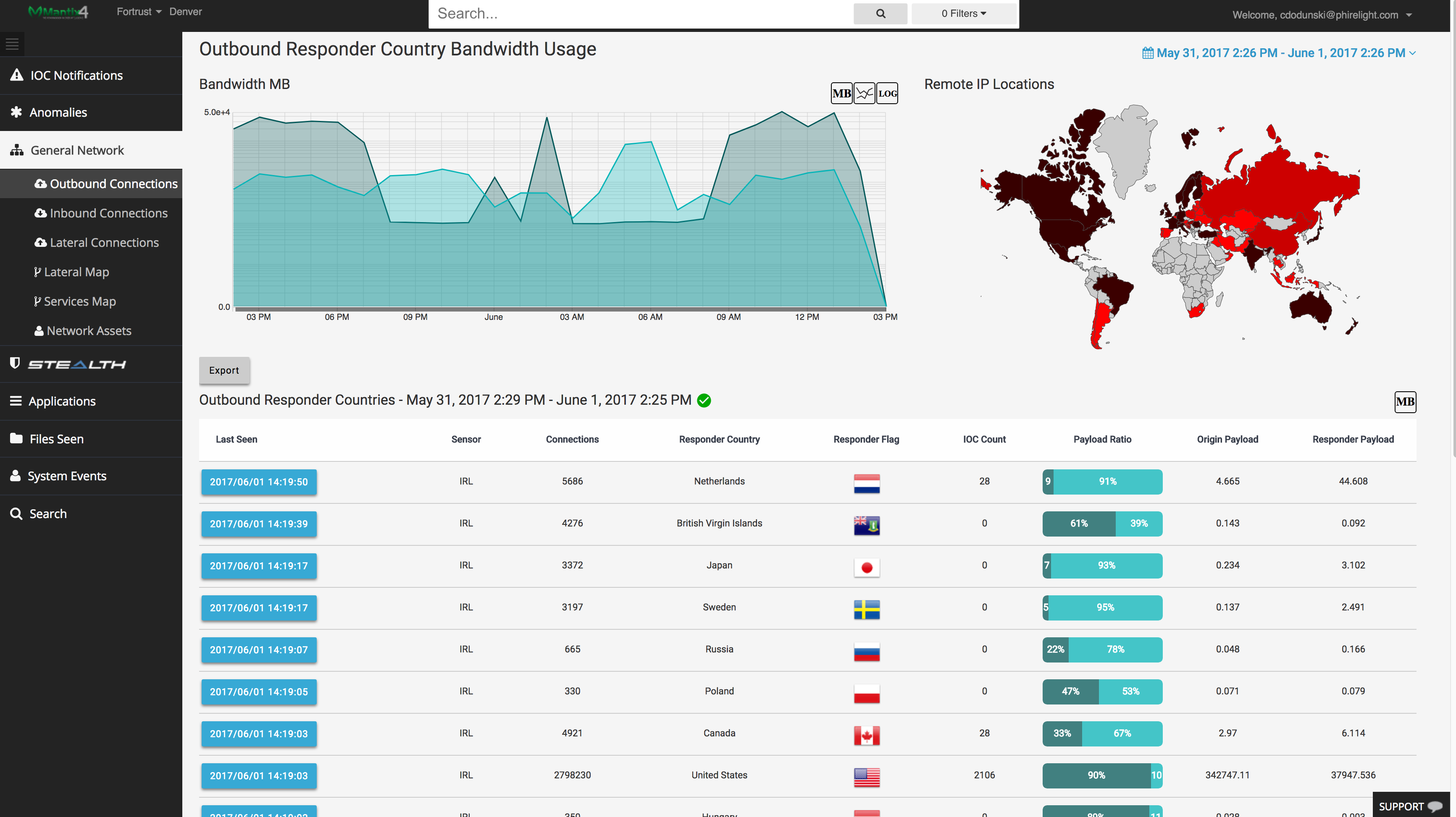
Within 24 hours of installation, the Mantix4 platform is proactively collecting and displaying actionable information about inbound, outbound and lateral traffic. Mantix4 leverages advanced threat intelligence, big data analytics, and behavior anomalies, to give users context-based threat intelligence through a highly-visual platform. M4’s Cyber Hunting platform can even detect and neutralize sophisticated breaches, including advanced malware that can ‘play dead,’ and lie dormant in a company’s systems for months.
Mantix4’s proprietary EPIC Endpoint Agent Software brings Advanced Behavior Monitoring, Threat Detection, and enhanced Cyber Hygiene Assessment for endpoint and cloud services enabling continuous hardening of your IT environment against Cyber threats.
Sustained improvement. We are continuously innovating and adapting to new attacker tactics, techniques, and procedures. We study malware developments and movements and use algorithms to track long-term trends. By collecting data about interactions and behaviors of threats and feeding that data back into the Mantix4 Platform it becomes smarter and generates more effective threat intelligence.
Mantix4 Threat Hunting
Mantix4’s Cyber Threat Hunting Platform, originally developed by a team of Defense Intelligence, Cybersecurity, and Military experts, accelerates the Cybersecurity team’s hunt enabling proactive defense against cyber threats. The Mantix4 platform meshes critical human intuition and analysis with advanced machine learning to proactively and persistently analyze, hunt, disrupt and neutralize the most dangerous Cyber Threats.
Instead of spending months deploying technologies that attempt to sift through false positives, Mantix4 installs in under an hour, integrates necessary information, and empowers IT professionals to proactively cyber hunt effectively bridge the visibility gap.
Mantix4 Incident Response
While our priority is to prevent your worst fears from coming true, the reality is you are under attack. Data breaches, ransoms, and other nefarious action take place daily. If you have suffered this fate, Mantix4 and our Partners’ top-tier Cyber teams are here and ready to help you.
Mantix4 SOC Enabler Platform Works for You
Mantix4 deploys rapidly and delivers integrated full-context visibility of Network, Behavioral, EDR/XDR, Q-Net, and other platforms generating proactive actionable Cyber Intelligence and reduced Risk. And if you prefer to outsource your SOC, we can provide the full-turnkey solution.
Mantix4’s revolutionary technology bridges the large visibility gap left by traditional security technologies. Instead of spending months deploying technologies that attempt to sift through false positives, Mantix4 installs in under an hour. Within 24 hours, the Mantix4 platform is proactively collecting, integrating the necessary data, and displaying actionable information. Empowered IT professionals with targeted full-context integrated alerts can proactively limit and eliminate network compromises.
Mantix4 leverages advanced threat intelligence, big data analytics, and behavior anomalies, to give users context-based threat intelligence through a highly-visual platform. Mantix4’s Cyber Hunting platform can even detect and neutralize sophisticated breaches, including advanced malware that can ‘play dead,’ and lie dormant in a company’s systems for months.
The Mantix4 platform is delivered over the cloud in a Tier III Gold Certified Data Center. Customers can purchase the platform directly, or it can be managed by Mantix4 and our Partner’s anti-cyber-attack teams.
Mantix4 integration with Microsoft and other business manager systems automates ticketing and workflow management generating Security Operations Center (SOC) efficiencies and scalability and reduced risk.
Monitor
Managing and monitoring your network security is both time-consuming and expensive. Mantix4’s cybersecurity monitoring system helps MSSPs deliver unmatched insight and control of security threats for your organization. Mantix4 delivers a cloud-based, managed security and monitoring service designed to help existing SOC teams analyze end point and network security events, perform alert triage, and escalate confirmed threat notifications for appropriate expert response – 24x7x365. Best of all, Mantix4’s analyst dashboard is a force multiplier for SOC teams, extending their reach, reducing alert fatigue and increasing productivity.
Network
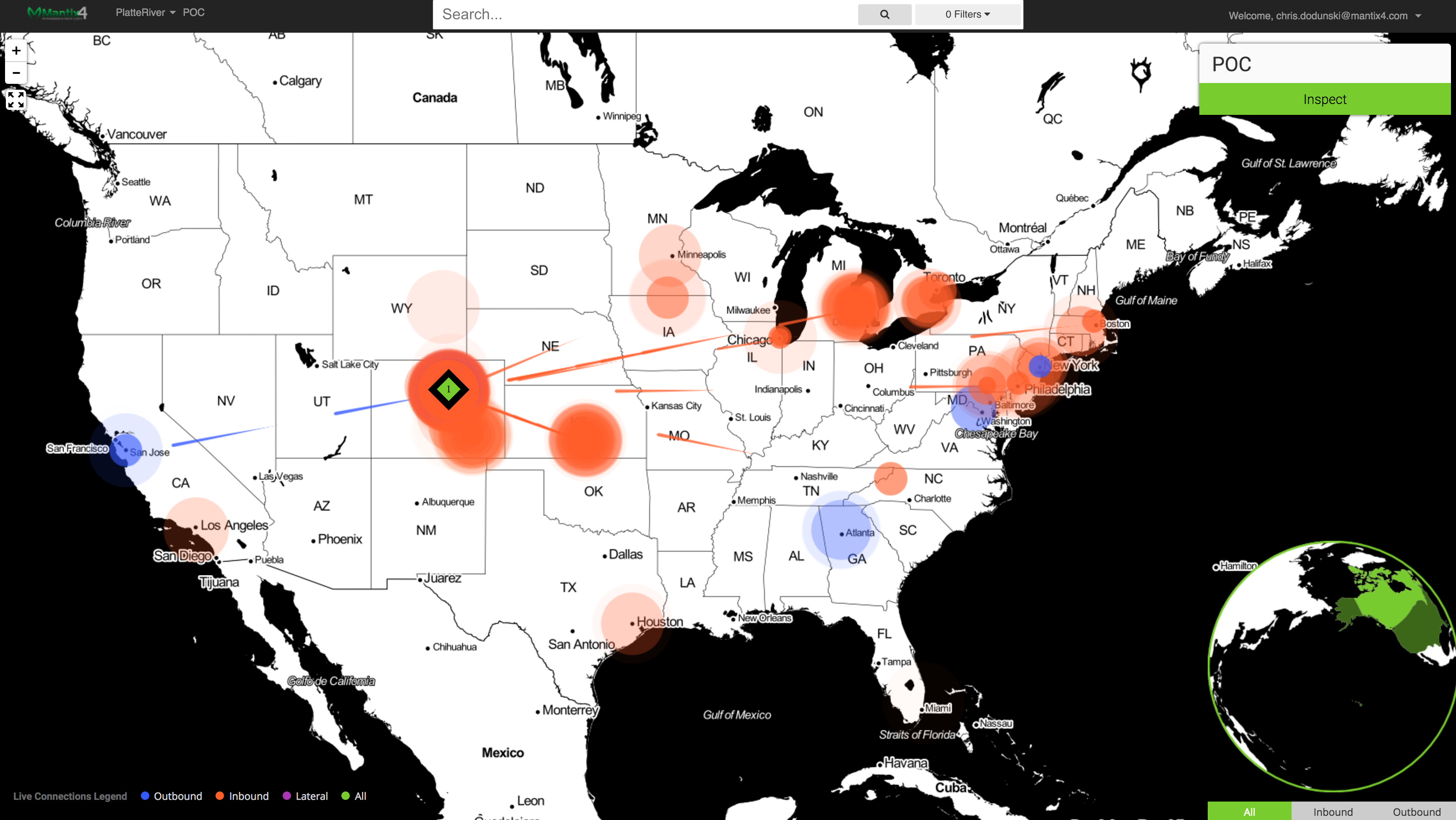
Cyber criminals are succeeding at unprecedented rates, wrecking small businesses and causing cyber insurance carriers to raise the bar for writing coverage and approving claims. At the heart of this new crime wave are network-based attacks allowing predators to hide from perimeter, endpoint and SIEM platforms. Mantix4 provides the missing piece, delivering network context and better analyst experience to help SIEMs and EDR/ XDR rise to the task. Mantix4 captures network activity with telemetry from different altitudes to fill in the blind spots and empower SOC analysts intervene before attackers can escalate.
End Point
Attackers know endpoints matter; the workstations, laptops and servers where users and applications go to access data and the Internet. Mantix4 integrates end point alerts with its network and threat hunting metadata to provide analysts with full-spectrum visibility. End point events like login attempts and directory copying can be correlated with patterns like lateral movement to give Mantix4 analysts visibility into the patterns within log data in your client environments – to understand what’s anomalous and in need of investigation.
Threat Hunting
Mantix4 enables enterprises to proactively and forensically identify, visualize and disrupt would-be attackers. Threat hunting turns an analyst from a beat cop into a detective, working on the assumption that an attacker is already in the network. Mantix4 lets analysts dig deeper, displaying indicators of compromise, lateral movement and other tell-tale artifacts that may uncover evidence of attack behavior. It also performs pattern matching against threat intelligence libraries of hackers’ sources and methods to help analysts get out in front of a breach.
Your turn to make a move
Like Nothing You've Seen. Book a Demo Today & Experience Mantix4
Book a discovery meeting todayHigh Fidelity
See inbound, outbound and lateral threats in your network in High Fidelity clarity for the first time, in real-time. Gone is the ocean of false positives that blind most security teams. Many products try to offer intelligence, when what you really need are answers. Mantix4 provides answers, lightning-fast, accurate, actionable and reliable. You are always just a few clicks away from identifying known and unknown threats, right down to an infected IP address in your network.
Schedule a demo today and see the difference in High Fidelity from Mantix4.
Proactive
Mantix4 changes the rules of asymmetrical warfare. An enterprise security team isn’t truly proactive until it is cyber-hunting known, unknown and advanced threats. With continuous monitoring and deviant behavior collected throughout your networks, Mantix4 also correlates intelligence from over 40 different threat feeds gathered by commercial, open source, private research and government white hats. We will continue to add threat feeds, especially from the Dark Web as they become available. Imagine proactively going after threat actors by using “canaries” and “honeypots” using the Mantix4 Forensic State Analytics tool!
Schedule a demo today and see the difference in Proactive security from Mantix4.
Automated Security Orchestration
When securing your organization, time is your enemy. Many approaches automate post-breach forensics, but by then the damage is done. The sheer magnitude of security logs and alerts, including the false positives, can paralyze and rob precious time from your security team. Mantix4’s High Fidelity visibility and automation is 30X faster than traditional manual efforts. Automating your Threat Management with cyber-threat hunting and remediation eliminates the lost cycles spent on reactive security energies that often fail to identify threats that have been dwelling in your network for months.
Schedule a demo today and see the positive impact on your security team with Automated Security Orchestration from Mantix4.
